In A Cryptographic System What Properties Should The Initialization Vector Have
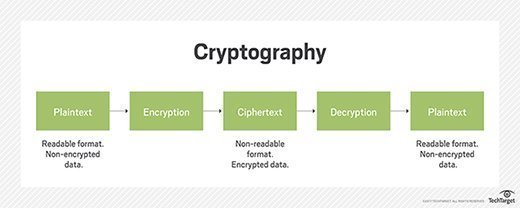
In a cryptographic system what properties should the initialization vector have. Which type of block Cipher changes the position of the characters in a plain text message. Creates a symmetric decryptor object with the current Key property and initialization vector. Initialization vector is a continuously changing number used in combination with a secret key to encrypt data.
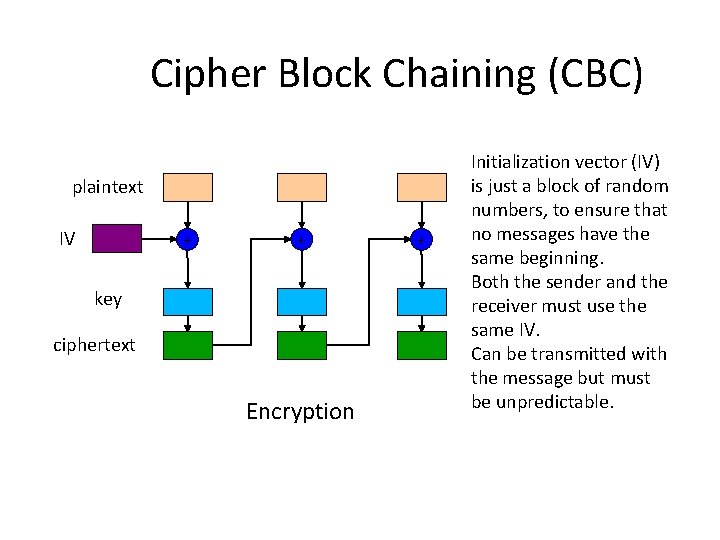
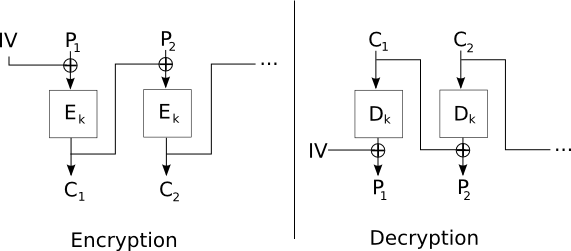
Initialization vectors IVs are used to prevent a sequence of text that is identical to a previous sequence from producing the same exact ciphertext when encrypted. In cryptography an initialization vector IV or starting variable SV is an input to a cryptographic primitive being used to provide the initial state. Also as Bruce Schneier notes in Applied Cryptography Even worse two messages that begin the same will encrypt the same way up to the first difference.
In a cryptographic system what properties should the initialization vector have. The bcrypt utility produces an enhanced key that is 128 bits long. In a cryptographic system what properties should the initialization vector have.
In a cryptographic system what properties should the initialization Vector have. Some symmetric ciphers use an initialization vector to ensure that the first encrypted block of data is random. GCM mode EAX mode and CCM mode satisfy this requirement.
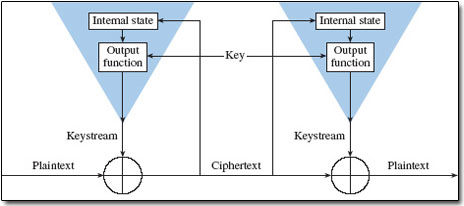
The IV initializes the algorithm to process the message. An IV is a public value which impacts the encryption process. The IV is typically required to be random or pseudorandom but sometimes an IV only needs to be unpredictable or unique.
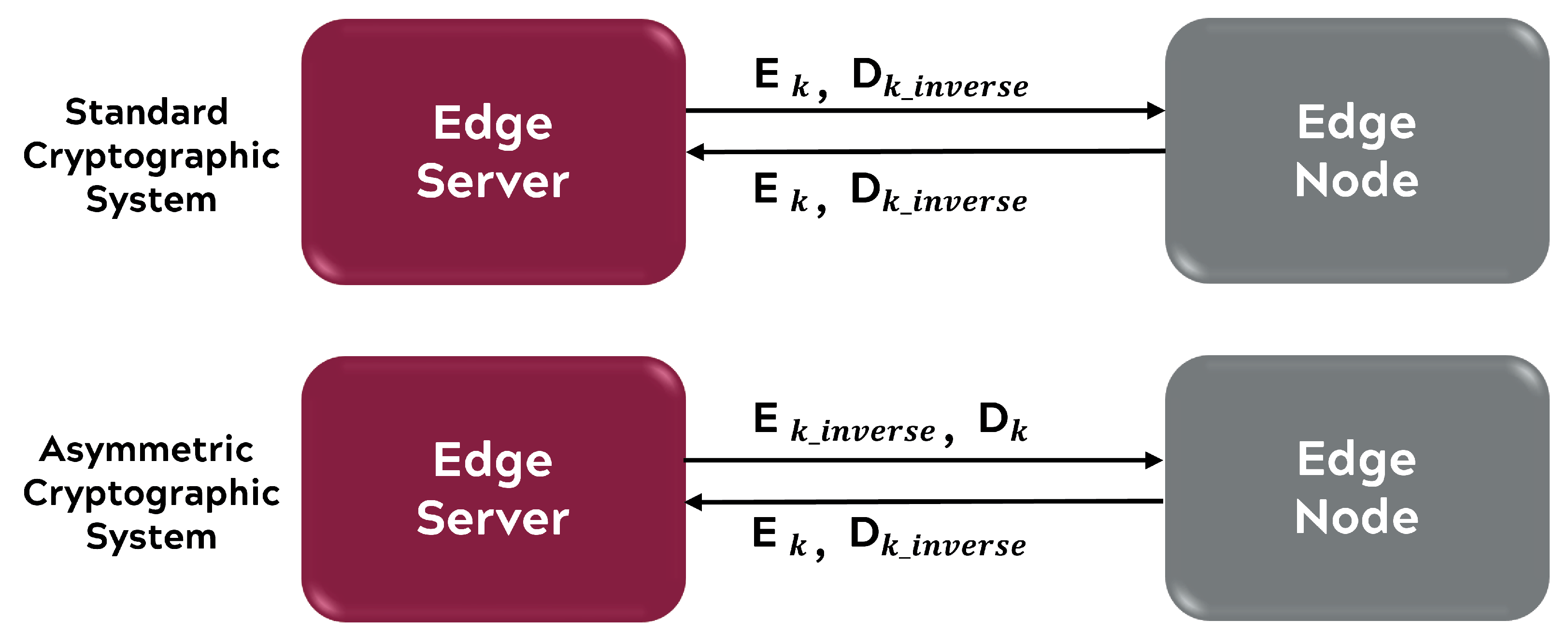
What is the cryptography mechanism that hides secret communication within various forms of. CreateDecryptor Cria um objeto descriptografador simétrico com a propriedade Key atual e o vetor de inicialização. You are concerned about the strength of your cryptographic keys so you implement a system that does the following.
The initial key is fed into the input of the bcrypt utility on a Linux workstation. Non-authenticated encryption modes can allow attackers to modify ciphertexts in ways that have well-defined effects on the underlying plaintext.
In a cryptographic system what properties should the initialization vector have.
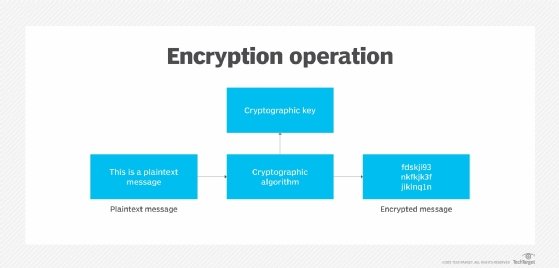
Learn vocabulary terms and more with flashcards games and other study tools. In a cryptographic system what properties should the initialization vector have. An IV is a public value which impacts the encryption process. To prevent an attack an IV must not be repeated with a given key and should appear random. Typically there will be many IVs that are used with a single key. Of course you may have input that is smaller than a given chunk size or the last chunk of input might not be sufficient to fill an entire block so you can use padding to fill out the input size to match the right chunk lengthAn initialization vector is a random seed that is used to defeat attacks on a cryptographic system. Deterministic IVs in Algorithms. For security the initialization vector should be large and it should be unpredictable. The initial key is fed into the input of the bcrypt utility on a Linux workstation.
The bcrypt utility produces an enhanced key that is 128 bits long. When the initialization vector is large and unpredictable an encryption algorithm can generate secure keys or encrypt data that is difficult to decrypt. If you want to generate hard-to-guess symmetric keys just use a cryptographically-strong source of random numbers. In a cryptographic system what properties should the initialization Vector have. The IV initializes the algorithm to process the message. Q3 In which of the following cryptographic methods is the order of the units in the data rearranged to form the ciphertext. The bcrypt utility produces an enhanced key that is 128 bits long.

























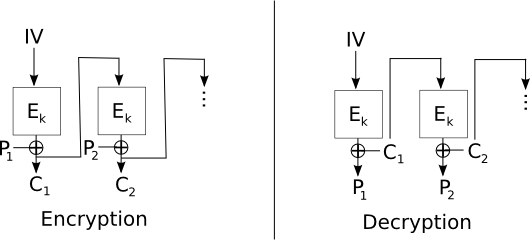




Post a Comment for "In A Cryptographic System What Properties Should The Initialization Vector Have"